What's in his Outlook mailbox?
The history of Drive Badger began around April 2017. There was some investigation, and officer behind it wanted to search someone's mailbox (very big PST file) without being noticed. It was finally exfiltrated using 7-Zip and a simple batch file, but the idea was born.
Development has started
Around 25-26th May 2017, first scripts were made. For Windows first. Development lasted for about 2 months and the result was never open sourced - since it works on Windows level, it would be to easy to burn it. This product is now sold as Sherlock.
The final outcome of this phase was knowledge, that Sherlock solves client's requirements only partially. So another solution was born - this time based on Raspberry Pi Zero and Raspbian Linux.

Dirty Harry v1
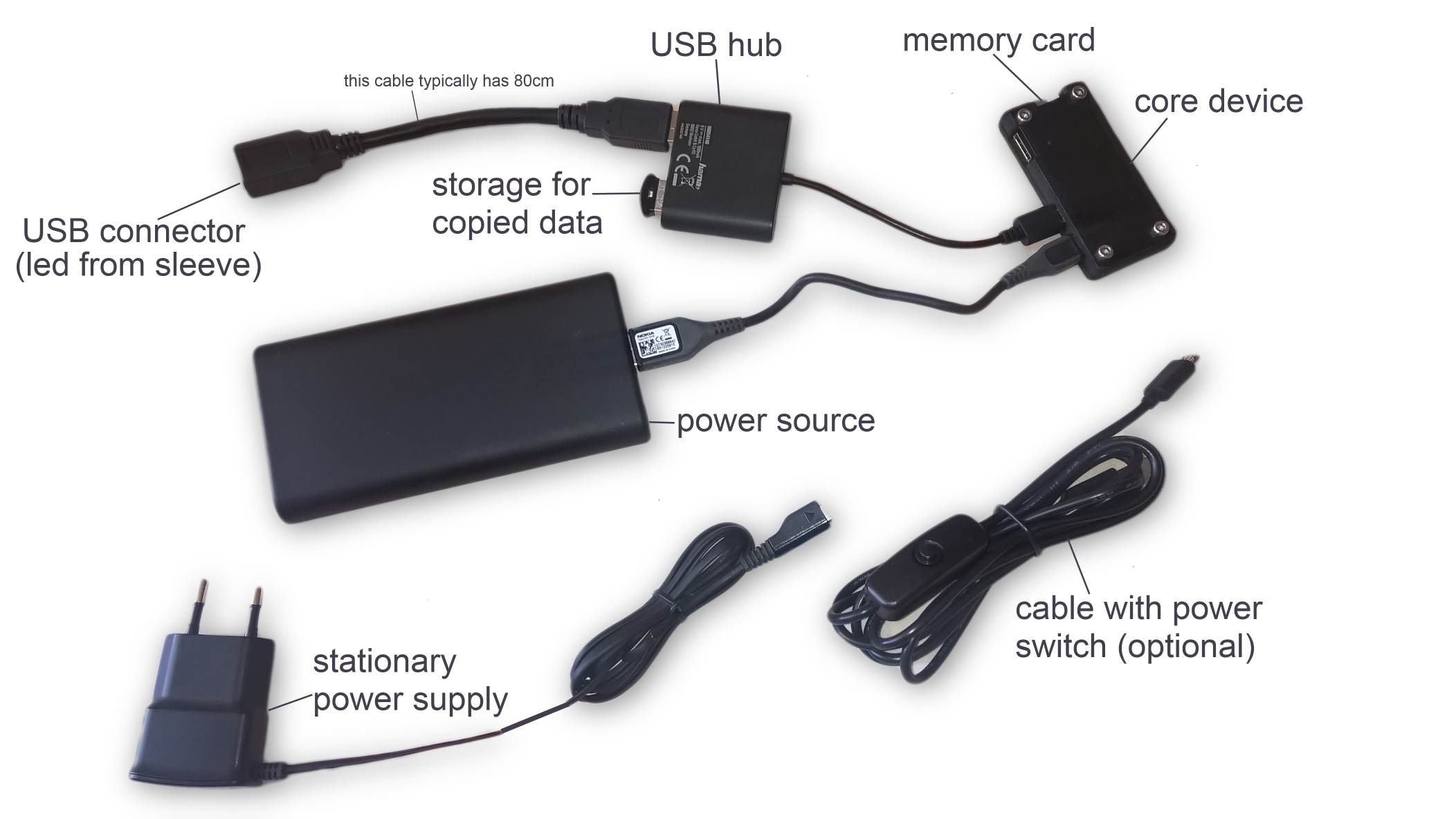
This is exactly how it was presented to clients, and how it worked: Raspberry Pi Zero in custom case, Anker Slim power bank and a few accessories. Everything came with dedicated changes to the uniform pants to hide the power bank, done by professional sewer.
From 3 pieces of Raspberry Pi Zero and 2 custom cases that we initially bought for the project, 2 were sold (including the one on photo).
Polish sex business infiltrated
Both sold Dirty Harry devices were used to infiltrate polish sex businesses (in 2 different regions of Poland). Both times with success. At least one investigation was provided with enough evidence primarily thanks to Dirty Harry capabilities.
Until 2019, over 20 escort agencies were raided and closed down partially thanks to evidence or knowledge acquired using just 2 sold Dirty Harry devices...

Dirty Harry v2
First version was quite limited: it worked blind, without giving any signs to the user, if the copying was finished. Maybe except blinking the small LED on the target hard drive - but only if the bigger model with LED was chosen. Also, Anker Slim power banks suffered overheating.
Second version came with Pimoroni Blinkt display, with 8 multicolor LEDs, showing color codes, power banks replaced with PQI, and series of commercial add-ons (see below website photo).
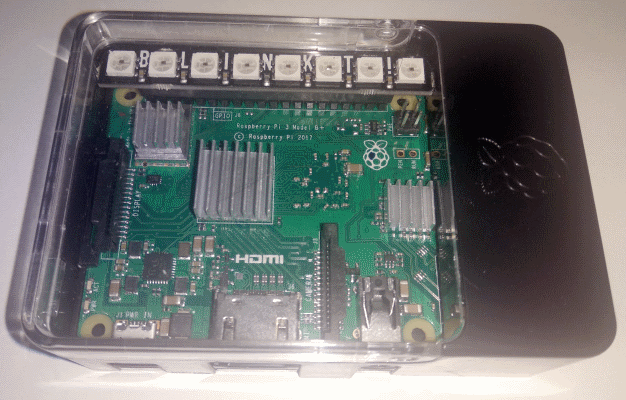
New website, but soon...
Shortly after releasing Dirty Harry v2 and the new website, we were asked by our back-then-the-most-important client, one of polish software houses, to hide the project, since it imposes the risk for them.
We were also aware, that further using "Dirty Harry" name will be complicated from legal point of view, when it becomes known outside IT world. So we decided to hide everything under this name, until we decide, how to reshape everything.
Covid-19
Covid-19 was a total game-changer for thousands companies and employees in Poland (and probably in the whole world). The software house, that asked us to hide the project, degraded from the most important client, to one of many parallel clients, possible to leave behind in case of disagreement on long-term priorities. And we actively started thinking about new brand name.
Planter aka. Harry aka. Dirty Harry v3
We were aware of the problems with "Dirty Harry" brand. So we split the name: Planter for the open source project on Github etc., and Harry (later rebranded to Mobile Badger) for the commercial part.
Version 3 brought the huge change to the product. The code was almost fully rewritten, as modular as possible, and Planter device was able to utilize different LED displays, not only Pimoroni Blinkt: each driver could map universal "events" into colors, texts etc.
Raptor
We started working on another software solution, which we initially named Kali, and shortly rebranded to Raptor. On August 1st, we released the initial open source version. It was developed under that name until March 2021.

Drive Badger
Raptor was rebranded to Drive Badger, and fully open sourced. 100% of production-ready code was released completely for free, and over 100 pages of technical documentation were written to help non-technical users to understand both the product and attack techniques.
It was also a philosophical change for us. While we still need money for expanding our hardware testing lab, we no longer want to earn anything for ourselves. Drive Badger is, and will be, 100% free.

Mobile Badger aka. Dirty Harry v4
In the meantime we decided to rewrite Planter (Dirty Harry) once again, reducing over-modularity and leveraging Drive Badger functionalities, eg. support for hard drive encryption. It's nearly ready.
We are also constantly expanding our hardware testing lab. This allowed us to add early support for Windows 11. Not because it's required for real exfiltration attacks at this point, but to demonstrate, that we can.
The Hack Summit 2021
We were invited to leading polish ITSEC conference with 3 lectures about Pegasus data interception platform. On 5th November we compared it with several commercial competitive platforms, and also with Drive Badger. Note: movie in polish language.
Support for different display devices
It started in 2018 from support for Pimoroni Blinkt device. Now we wanted to expand this area, from 2 dedicated drivers to subproject, focused just on mapping Mobile Badger events to particular display effects (depending on display device capabilities).
Our goal is to allow deepest possible integration of our tools with equipment already owned by the user - thus flattening the learning curve.
You can find the latest project news here.
Make world a safer place
Become our sponsor
From the founder...


