Drive Badger is sometimes being compared to, recently popular in media, Pegasus spyware platform, developed by Israeli company NSO Group. In this article, we'll try, without going too far into technical details, to compare the functionalities of both platforms from purely functional side.
From technical point of view, Pegasus can be divided into several dozen separate functional modules (mostly related to remote infection and subsequent analysis of the victim's actions). But functionally, looking from the perspective of surveillance officer, it can be divided into 5 functional blocks:
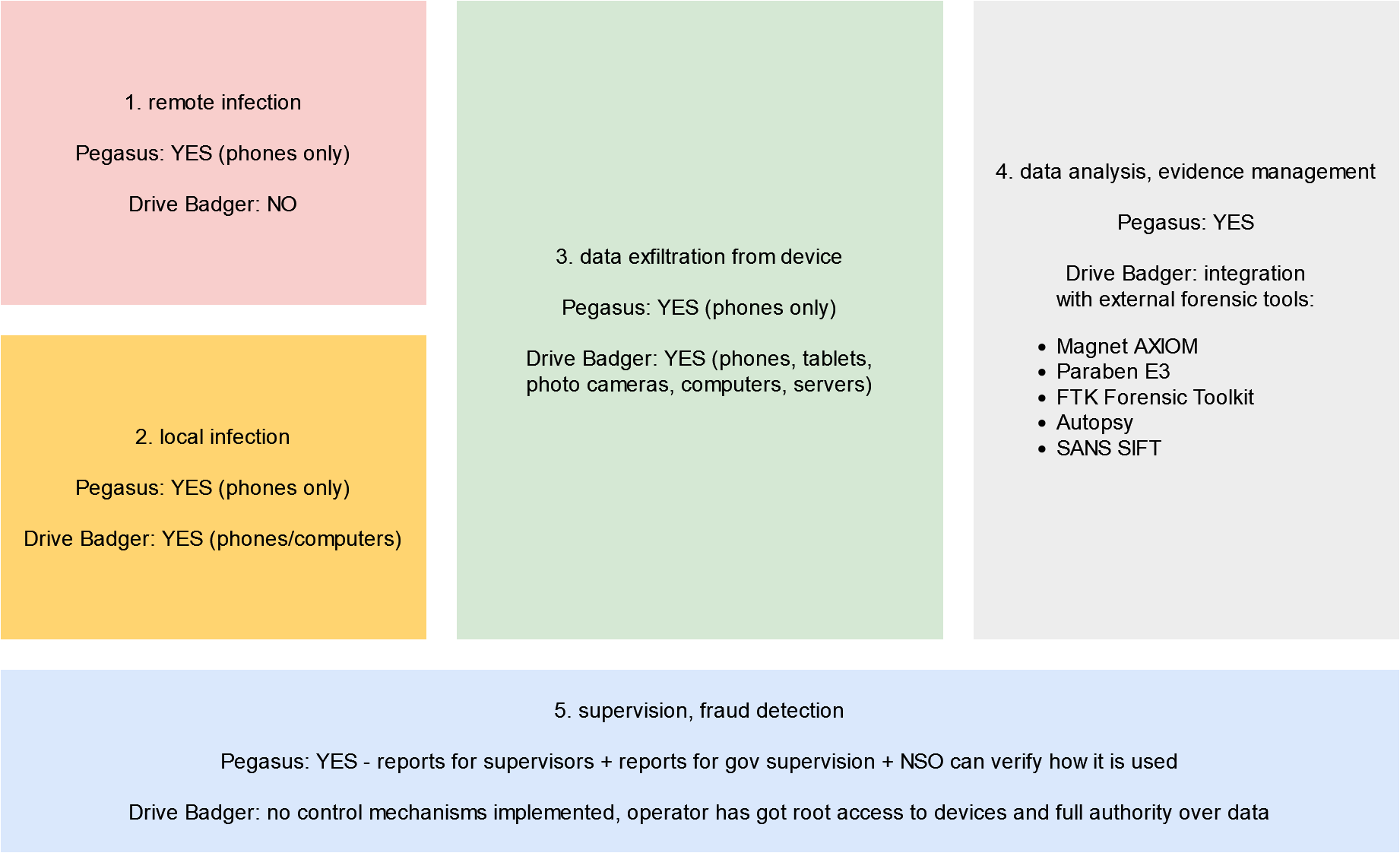
1. Remote infection
Fully remote phone infection ability is in fact the main competitive advantage of Pegasus and the reason, why it is chosen by uniformed services across the world above any other platform - including platforms with much better digital evidence analytics. Especially that Pegasus supports phones and tablets only, and it's not possible to combine evidence obtained from victim's phone and computer in any single tool.
2. Local infection
Drive Badger can "infect" only locally - but full range of targets: computers, servers, mobile phones, tablets, pen drives, and even photo cameras. This functionality was developed for countries, where evidence or backdoor planting is legal, eg. Brasil, Vietnam, China and so on.
As Drive Badger is developed by a civillian company, without any cyberweapon trading licenses etc., as open source project, it is not directly weaponized (apart from this simple demo for Linux hosts). It fully allows injecting content into exfiltraded filesystems, but it is operator's responsibility to provide any exploits, evidence files or any other content to be injected.
3. Data exfiltration
While Pegasus' main competitive advantage is remote infection, Drive Badger excels in efficient data exfiltration, with support for all important disk encryption methods and automated key matching.
The whole data exfiltration process is fully automated, based on over 400 unique exclusion rules (for various operating systems, for both phones and computers), which reduce the amount of files to be copied by eliminating low-value files and directories from the list, thus save most of the time, that would be spent by "naive" script.
4. Data analysis and correlation, digital evidence management
Pegasus comes with web panel for surveillance officers, allowing them to browse phone contents in a way similar to how most people uses Google services (especially Drive and Calendar): browse SMS contents, call lists, photos, calendar entries etc.
Drive Badger mainly focuses on quick taking control over victim's data, while all analytics is left to be done using 3rd party computer forensic software (either commercial or also open source).
Compatible analysis tools
Below we intentionally skipped tools that:
- don't have an open source, free, free for personal use, trial or demo version - or even a commercial version with reasonable price, that could be paid for just 1 month
- can work only:
- in original LAN (eg. Wireshark or other network traffic analyzers)
- on the original computer (eg. Volatility Framework, or otherwise awesome Nirsoft tools)
- on a block image of the original drive (eg. most file recovery tools)
Magnet AXIOM
It's a definite leader among forensic analytics tools. AXIOM package consists of 2 separate tools: Process and Examine (in one you operate on raw source materials, while the other is for conducting evidence analysis - of course this makes sense during formal investigations, where all knowledge is collected for use in the trial - while Drive Badger is designed for collecting operational knowledge).
AXIOM is a paid (and expensive) toolkit. Official trial version is available, however it requires not just filling the registration form, but also being verified by Magnet Forensics. In Internet, it's also easy to find cracked versions 4.10.0.23663 and 3.11.0.19007, without malware.
Paraben E3
Another commercial tool, in our opinion even better than AXIOM (especially when analyzing non-Windows platforms, eg. Apple devices) is Paraben E3, which has a free version - functionally restricted, but fully functional regarding phones.
Registration is just a formality and the download link comes in email right after completing the form.
FTK Forensic Toolkit
If you know the very popular, free FTK Imager software - FTK Forensic Toolkit is a full forensic analysis suite, developed by the same company.
The trial version can be simply downloaded, without any previous verification, or even registration form.
Autopsy
The above 3 packages are commercial, very expensive tools, with proprietary solutions for working with digital evidence - so user can operate not only at raw data level (eg. photos, SMS history etc.), but there are higher, abstract levels: evidence and investigation.
Different types and parts of raw data can be grouped together, forming an evidence. And evidence can be attached to investigation. Finally, these data can be exported in imported, which, especially for AXIOM, allows cooperation of many experts on the same investigations directly in AXIOM, not just at the paper level.
Autopsy (often bundled with The Sleuth Kit, for analyzing drive images) is probably the only open source tool (comparing eg. to the below ones), that is not just a compilation of open source components, but provides its own panel, that at least tries to follow this commercial approach.
other open source tools
THe below recommended open source tools, are actually just specialized Linux distributions, based on either Debian or Ubuntu, with added bunch of generally known, open source, security-related programs: live forensic scanners, drive image scanners, filesystem scanners, network scanners, Windows registry scanners (eg. RegRipper), cloud content scanners, OSINT tools and so on, glued together in a better or worse way.
But still, different programs for each purpose, and working on raw data (computer or drive) level only, instead of uniform panel for investigators without IT experience.
- SANS SIFT - you need to register to download ready-to-run VirtualBox appliance, or alternatively you can download Ubuntu and WSL (Windows 10) installers without registration
- CAINE
- CSI Linux
- Parrot OS
- Kali Linux - exactly the same, which is the base system for Drive Badger
5. Supervision, fraud/abuse detection
Pegasus
In case both for Pegasus, and any other system to be officially approved as tool for armed forces:
- all activities related to maintenance and current usage of the system, are divided into roles and permissions - so the surveillance officer don't have access to global configuration, or even particular wiretap configuration, while people from technical support can't listen victims' activities
- there is a "four eyes principle", and it is required for all reconfiguration and wiretapping activities, possibly combined with review/versioning mechanisms (so one person is unable to do anything significant alone)
- surveillance officer is only a pawn, fully accountable for his actions
All these rules are intended to prevent abuse - both individual (eg. surveillance operator suspects his wife of infidelity and would like to spy her) and institutional (eg. spying politicians or journalists). In practice, since these restrictions don't really work in the first case, is it fair to still enforce them in the second one?
Drive Badger
Drive Badger is based on completely different assumptions:
- to start using it, you don't need any consent from your superiors
- surveillance officer has absolute power (root privileges) over his own Drive Badger/Mobile Badger devices, and over exfiltrated data
- all devices are privately owned by the surveillance officer (or organizer in case of bigger attacks)
- devices log only technical events (required for troubleshooting, and only internally), but nothing more
- target partitions (holding exfiltrated data) are encrypted, with up to 8 independent access passwords
- in case of physicall loss of the device, it can't be distinguished from regular Kali Linux Live without knowing the proper password
Of course, surveillance officer can still be held accountable for everything that happens outside the devices themselves - especially if their actions are recorded by cameras. Therefore, in each attack, there should be as little improvisation as possible, and as many strictly planned and rehearsed actions as possible.
