1. Too old hardware
Hardware so old, that their BIOS doesn't support booting from USB Storage devices.
Example: Sony Vaio PCG-7V1M / VGN-FE48M (Core 2 T5500).
Solution: most probably, such hardware is so old and slow, that it doesn't run any centrally-managed protections. So you can almost certainly safely exfiltrate data manually from working Windows. Or pull out the internal drive and connect it to another computer, or to Mobile Badger.
2. Booting from USB devices locked at BIOS/UEFI level + BIOS/UEFI password
You can try to open the device and disconnect the internal battery. However in most new computer models, this will only reset the internal clock and some basic settings, while passwords are kept in flash memory (non-volatile).
Additionally, you won't be able to restore the previous settings, so rather don't try this, unless it's a last chance for you. Instead try to pull out the internal drive and connect it to another computer, or to Mobile Badger.
3. Booting from USB devices locked at CPU level
Newer models of Microsoft Surface, that support secured-core PC architecture (eg. model Surface Pro X for Business), are protected against booting anything except pre-installed Windows 10. This mechanism is called Trust Boot.
Another mechanism, called Kernel DMA Protection, protects Windows from connecting M.2 drives (including through USB), that doesn't support DMA Remapping. Such devices won't be started, when connected without logged in user.
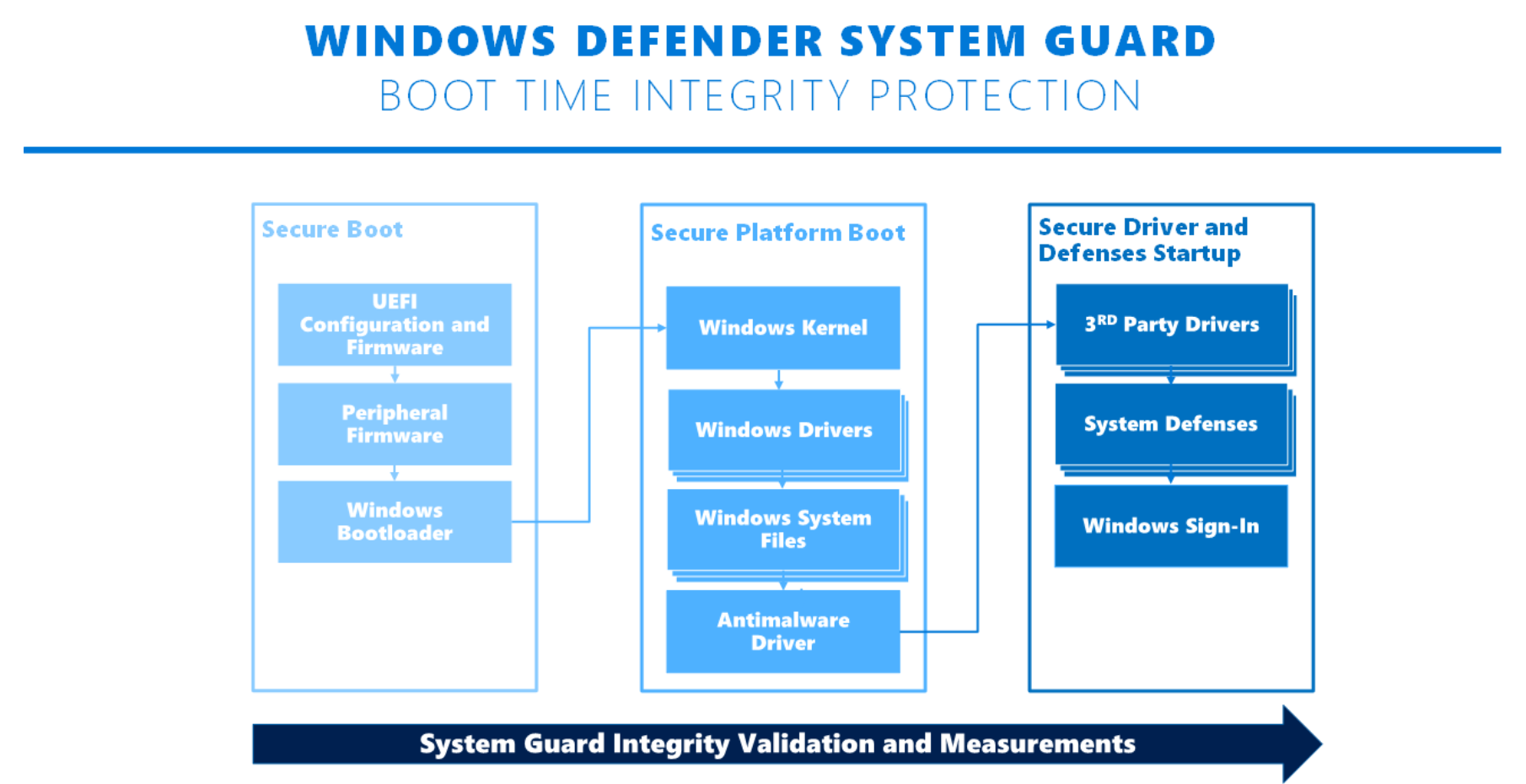
More technical details here (in polish language).
Currently we don't offer any solutions for this.
If you want to donate a working (not necessarily new) Surface Pro X to allow us to work on some solution or workaround, please see this page for the details.
4. USB ports physically disabled or damaged
See this page.
5. Windows 10 Home with TPM 2.0 and "drive encryption suspended", unable to obtain the recovery key
See this page.
