Drive Badger and Mobile Badger
Drive Badger is split into 2 separate products:
- Drive Badger itself, based on Kali Linux, meant for data exfiltration from "normal" computers (non-mobile)
- Mobile Badger, based on Debian/Ubuntu/Rasbian, meant for data exfiltration from mobile devices (phones, tablets, photo cameras etc.)
Drive Badger and Mobile Badger however share:
- most source code parts (and the same repository)
- the same exclusion rules
- the same drive encryption keys
- the same hooks
Design and usage safety
Drive Badger is built on top of Kali Linux. Thus it leverages mechanisms like:
udevdandsystemdfor actual hard drive identification- Kali persistent partitions feature, to encrypt the target partition using LUKS
- Kali Linux as such, to disguise itself (you can run anything on screen, while the attack is running in the background)
There is no way to distinguish between Drive Badger and ordinary Kali Linux, or to prove the fact of data exfiltration, until:
- someone knows the proper LUKS password
- it is caught in the act (including after the attack has finished, but Kali Linux is still working)
- you use the non-encrypted persistent partition (it is required for some old platforms)
Mobile Badger is built on top of Debian Linux with systemd version 229 or newer, or its clone, eg. Ubuntu, Raspbian or any other. More details are provided in its dedicated Wiki.
How it works
-
operator connects Drive Badger USB drive to victim computer
-
operator boots Live USB Encrypted Persistence
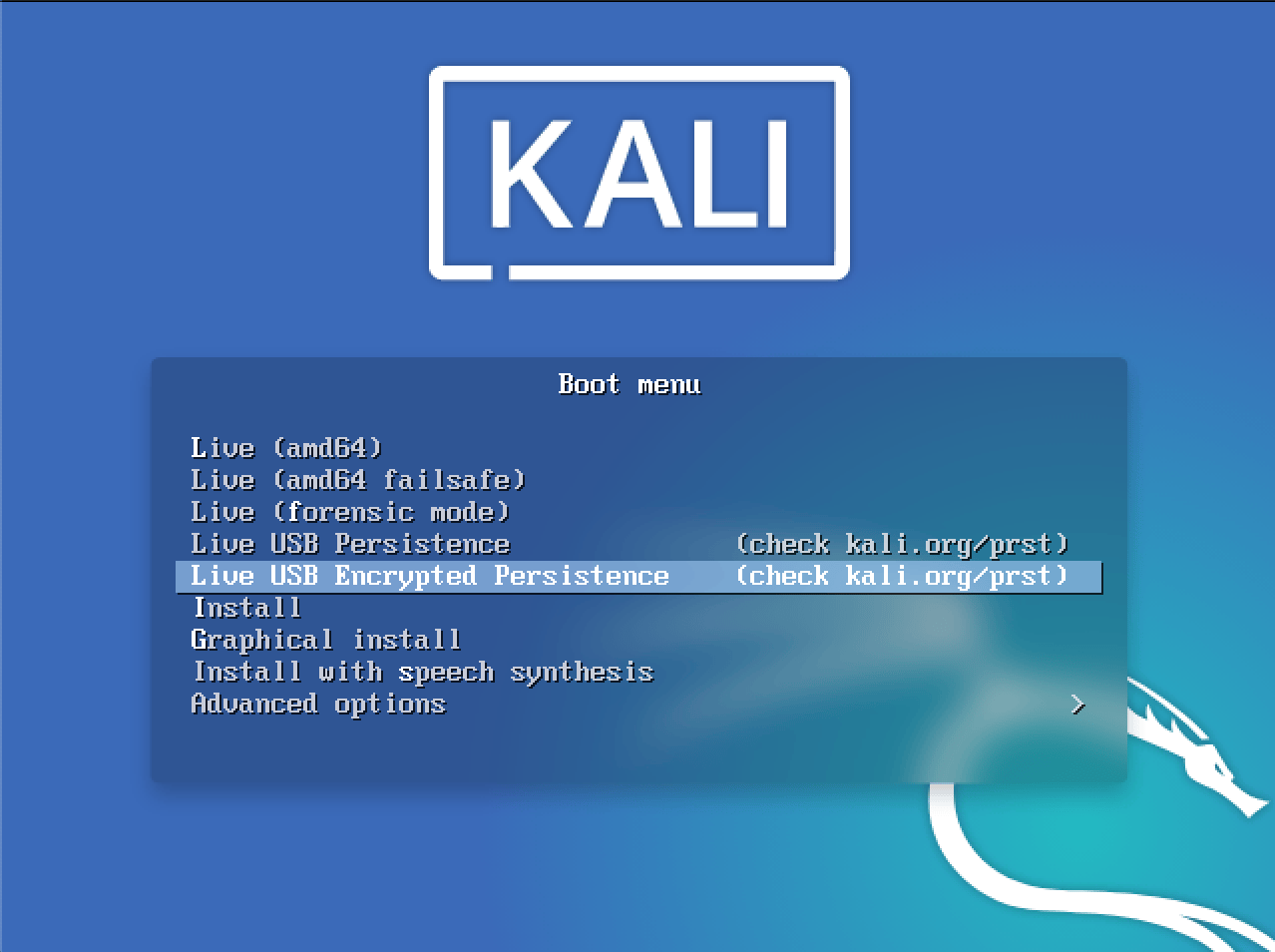
-
Kali Linux starts in text mode (at this point operator can run
startxto enter graphics mode) -
/etc/rc.drivebadgerscript is run in background -
it enumerates all local hard drives, including RAID devices, Bitlocked-encrypted drives etc., and makes a copy of "interesting" files (based on configuration rules) to special, hidden subdirectory on persistent partition
